How to address Let's Encrypt renew failure?

recently certificate for this site somehow got expired. It should got auto renewed. Since I added schedule event manually via crontab, Ghost cli also added one cron event while you run `ghost setup ssl`. I checked via `crontab -e`:
1 1 1 * * /home/errong_leng/.acme.sh/acme.sh --issue --home /etc/letsencrypt --domain errong.win --webroot /home/errong_leng/www/blog/system/nginx-root --reloadcmd "nginx -s reload" --accountemail errong.leng@gmail.com --force
2 2 2 * * /home/errong_leng/.acme.sh/acme.sh --issue --home /etc/letsencrypt --domain coca.errong.win --webroot /home/errong_leng/www/coca --reloadcmd "nginx -s reload" --accountemail errong.leng@gmail.com --force
53 0 * * * "/etc/letsencrypt"/acme.sh --cron --home "/etc/letsencrypt" > /dev/null
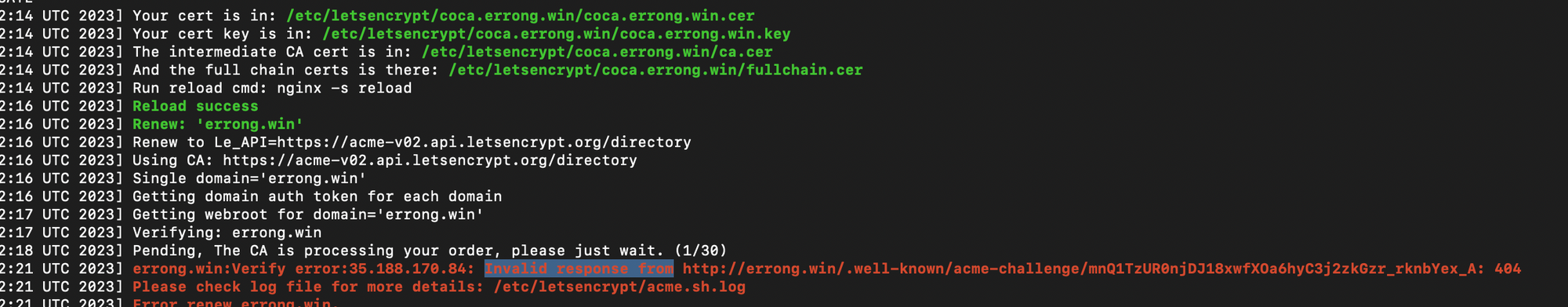
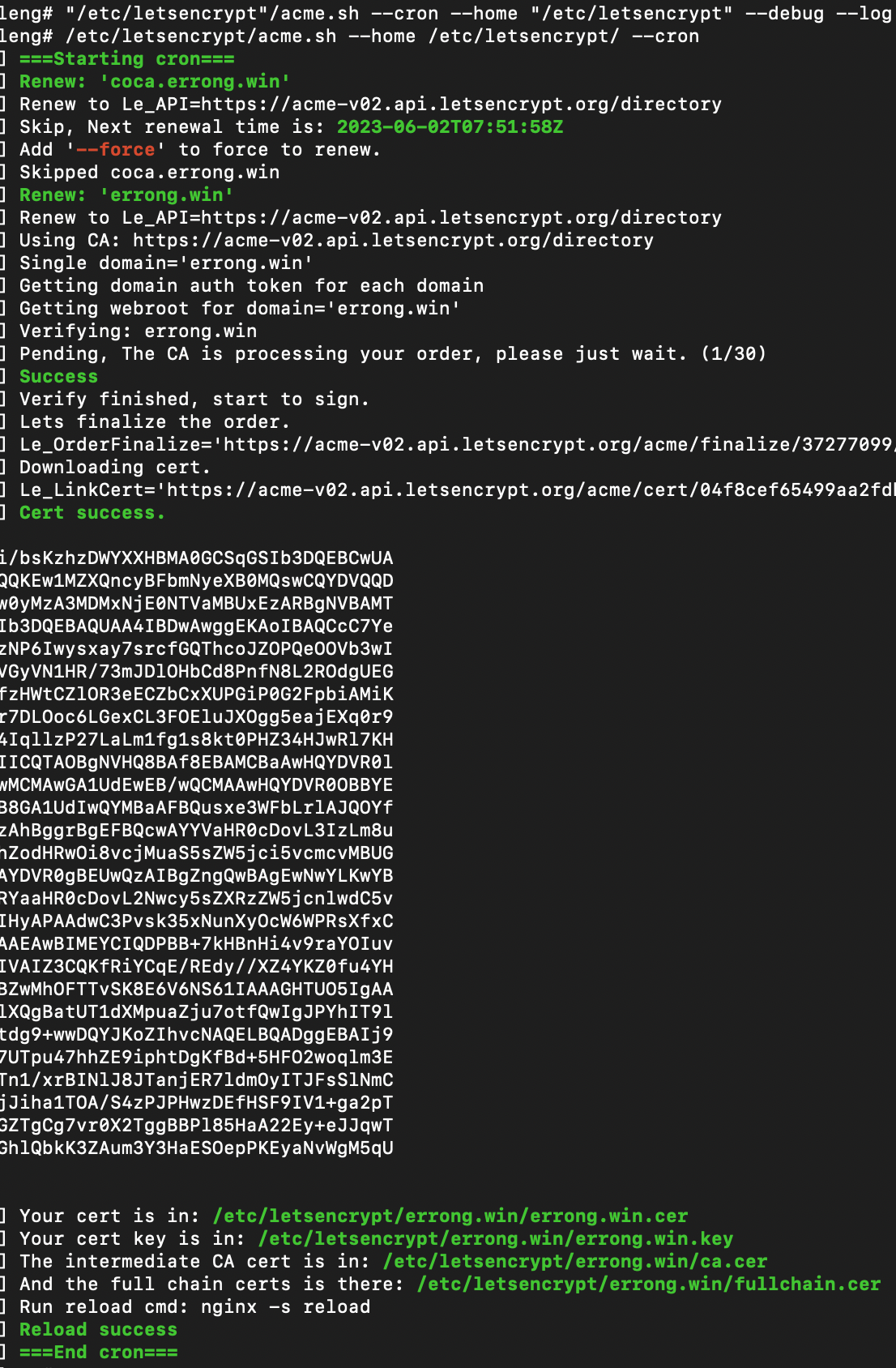
Then I tried manually run /etc/letsencrypt/acme.sh --home /etc/letsencrypt/ --cron, it did not work due to .well-know/acme-challenge/xxx 404 not found.
Acme.sh basic working practice
it takes 7 steps:
- generate new intermediate CA certificate
- generate /.well-known/acem-challenge/xxx to your server root
- renew via acme Le API, submit intermediate order to CA
- verifying the new cert by hitting http://{yourdomain}/.well-known/acem-challenge/xxx path
- Lets Encrypt finalize the cert once verification pass
- download the new cert issued by Lets Encrypt CA
- restart your server
For my case, it failed at step 4. My site uses nginx and .well-known path has been allow all in its conf.
location ~ /.well-known {
allow all;
}
Then check the /etc/letsencrypt/acme.sh.log, I found the root cause. Let's Encrypt acme.sh was still using the old root path /home/errong_leng/blog/system/nginx-root. In fact, I moved it to /home/errong.leng/blog/system/nginx-root since January.
[Tue Apr 4 17:14:52 UTC 2023] _currentRoot='/home/errong_leng/blog/system/nginx-root'
[Tue Apr 4 17:14:52 UTC 2023] wellknown_path='/home/errong_leng/blog/system/nginx-root/.well-known/acme-challenge'
[Tue Apr 4 17:14:52 UTC 2023] writing token:M5Hp4j3ELNj9t2x76zEF-bOMZzE4ZIVFLHTdm_T3Y5U to /home/errong_leng/blog/system/nginx-root/.well-known/acme-challenge/M5Hp4j3ELNj9t2x76zEF-bOMZzE4ZIVFLHTdm_T3Y5U
[Tue Apr 4 17:14:52 UTC 2023] Changing owner/group of .well-known to root:root
Where does Let's Encrypt acme.sh read the root path for your server?
I thought acme.sh would read the root directive from nginx configuration. below is the nginx ssl conf for my website.
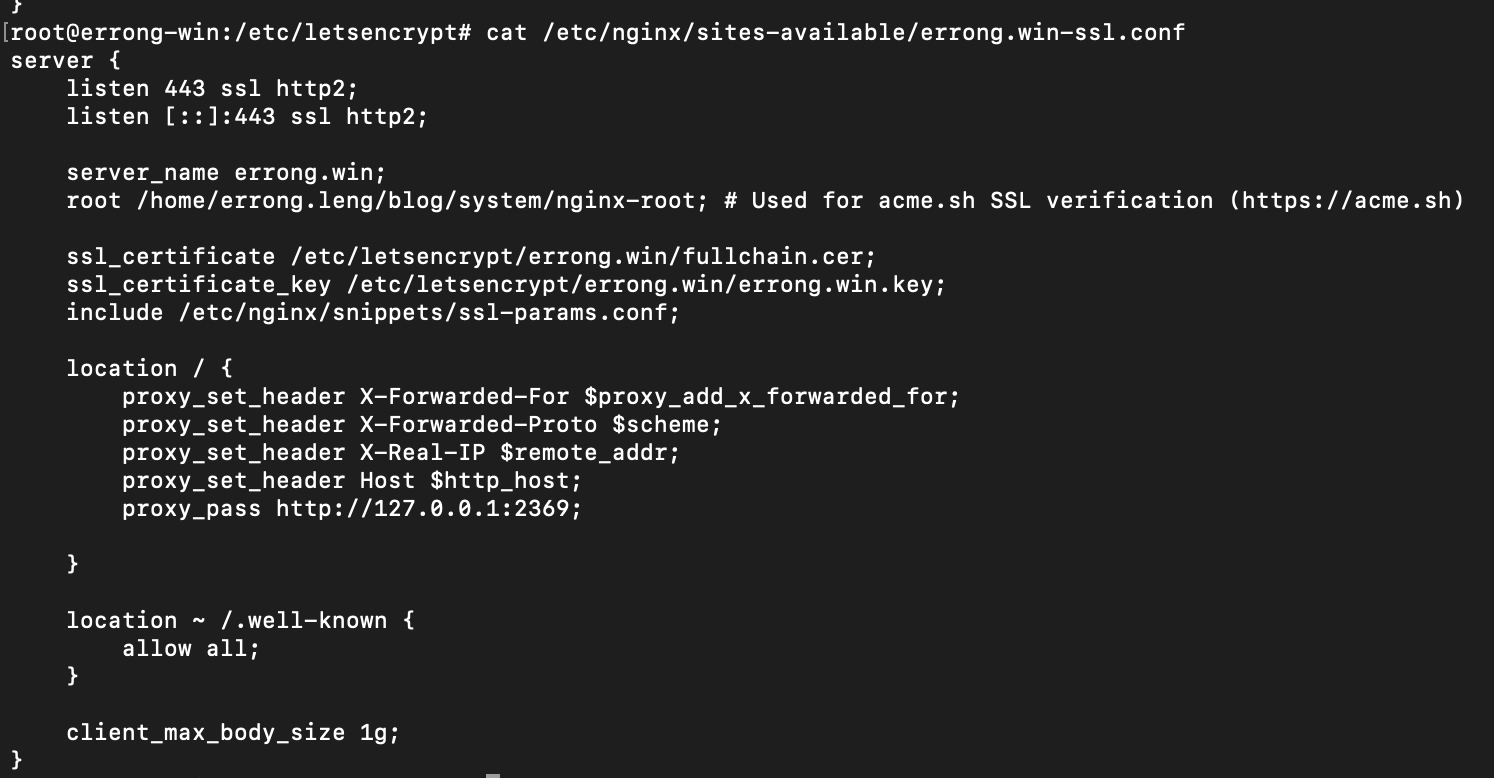
No, Let's Encrypt has its own configuration for your domain. I finally figure it out by checking '/etc/letencrypt' home directory. "Le_Webroot" defines the server root for your domain.
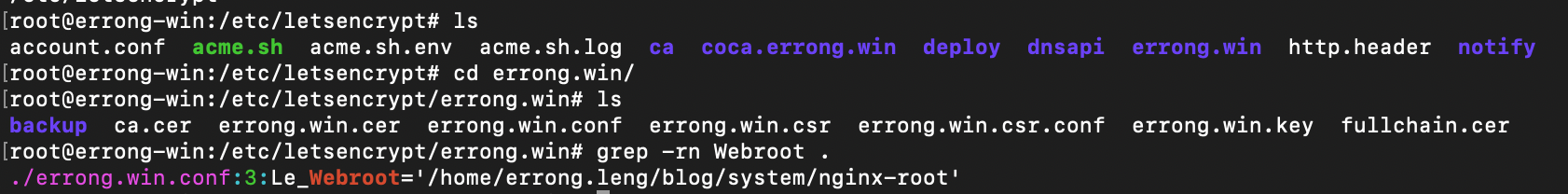
There was a typo error, so I fixed it and renew again, finally the cert got renewed successfully. I believe I don't need to work about certs ever more.
Failed Validation Limit
by the way, You should receive the following error message from your ACME client when you’ve exceeded the Failed Validation limit:
too many failed authorizations recently: see https://letsencrypt.org/docs/failed-validation-limit/All issuance requests are subject to a Failed Validation limit of 5 failures per account, per hostname, per hour.
To avoid reach failures rate, you can using let's encrypt's staging api to verify your SSL configuration before you set up for prod. In a word, add extra parameter to the acme.sh, --staging --test

Knowledge base: Ghost SSL setup
The CLI generates a free SSL certificate from Let’s Encrypt using acme.sh and a secondary NGINX config file to serve https traffic via port 443.
SSL configuration
After a successful ssl setup, you can find your ssl certificate in /etc/letsencrypt.SSL for additional domains
You may wish to have multiple domains that redirect to your site, e.g. to have an extra TLD or to support www. domains. Ghost itself can only ever have one domain pointed at it. This is intentional for SEO purposes, however you can always redirect extra domains to your Ghost install using nginx.
If you want to redirect an HTTPS domain, you must have a certificate for it. If you want to use Ghost-CLI to generate an extra SSL setup, follow this guide: